Iris Identification: General Overview & Advantages
Before iris anti-spoofing, there was an early concept of iris recognition that can be attributed to a 1953 clinical textbook Physiology of the Eye by F. H. Adler. The book stated that iris photographs could successfully replace fingerprints in terms of personal identification due to the unique characteristics of the iris. This assumption was based on a similar comment made by a British ophthalmologist J.H. Doggart in 1949, who was possibly influenced by Alphonse Bertillon's research on investigative biometrics.

The practical implementation of the approach began in 1993 when John Daugman published a work on an innovative computer vision algorithm, which was based on the idea that considerably high entropy in various iris sample classes can lead to better pattern recognition. Subsequently, he received a patent on the described technology in 1994. The first commercial iris-scanning system LG IrisAccess 2200 was introduced in 1999, contributing to the emergence of facial anti-spoofing and its types, countermeasures, as well as challenges.

Iris recognition has a few central advantages. First, it has 240 reference points for identifying a person, while a fingerprint has only 100 reference points. Second, it allows contactless identification, which is especially favorable in the light of the pandemic concerns. Finally, it is successfully used in certain countries like India where iris recognition is part of the UIDAI/Aadhaar program. But since it requires cooperation from a user, it is considered as an active liveness detection technique.

Iris Spoofing Attacks
Just like other biometric modalities, an iris recognition system is also prone to spoofing attacks. The major attack types highlighted by experts are: Zero-effort, Photo & Video, Contact Lens, Synthetic, and Postmortem Eye attacks.
Zero-effort attack
The most primitive attack type, in which no eye replicas or code manipulations are used. A perpetrator simply uses their own eye to get verified as someone else, which is possible in certain cases due to the False Match Rate (FMR). In turn, FMR is directly related to False Non-Match Rate when a legitimate person is denied access.
Photo & Video attack
This type involves Presentation Attacks (PAs). An image of a target’s eye retina can be obtained from their social media. The attack is made easier if a high-definition portrait was uploaded, which is possible since modern smartphones have high-resolution cameras (Isocell HP1 sensor offers up to 200 MP). Then the retina image is simply printed on photographic paper or replayed from a screen of a mobile gadget.

Contact Lens attack
A more demanding technique, it requires a lens that copies a target’s eye pattern as well as other unique properties. A textured lens allows superposing synthetic patterns either to masquerade or hide a perpetrator’s original iris pattern.

Synthetic Eye attack
The attack most difficult to execute involves creating a synthetic eye from scratch (glass eye). The method is mostly used in prosthetic eye surgery and employs plastic acryl. Averagely, it takes merely 3.5 hours to produce a prosthesis. However, copying the exact properties of a target’s eye and finessing the result requires a tremendous amount of effort, time and skill.


Cadaver Eye attack
Using a deceased person’s eye is also a potential attack scenario — similar to that observed in finger spoofing attacks. Currently, very few studies have been carried out on such a attack. However, iris recognition can be fooled using a detached or unconscious eye, as in some cases it scans only the eye surface (as opposed to retinal scanning).
General Framework for Iris Liveness Detection
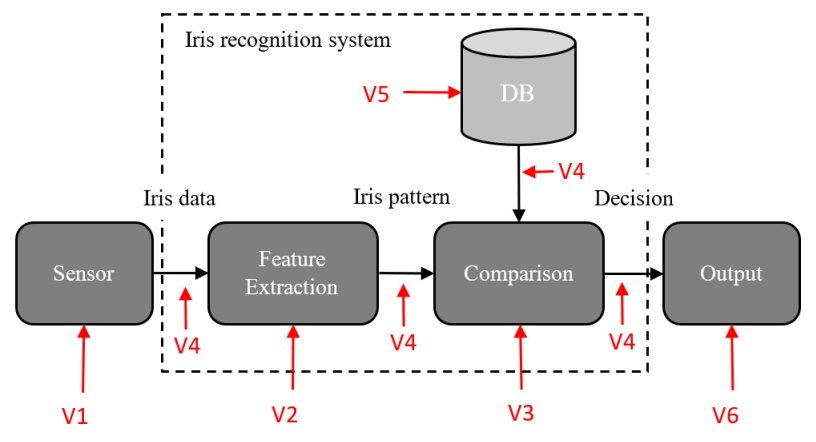
Commonly, an iris recognition system (IRS) includes the following components:
- Sensor. Commonly machine vision sensors CCD (analogue) or CMOS (digital) that capture the iris image are used.
- Feature extractor & Comparison module. These are software components responsible for segmentation, template generation, preliminary processing and comparison.
- Database. It contains vital data regarding iris templates and other necessary information.
- Communication channel & Actuators. This part involves internal and external communications: between system modules, mechanical actuators and cloud storage.
Correspondingly, all of these elements are vulnerable to certain attacks. For instance, sensors can be subject to PAs, databases can be tampered, feature extraction can suffer from malicious algorithm alteration, etc. Besides, an iris recognition system can be complemented with gait recognition, which makes it more of a passive liveness solution.
Iris Liveness Detection Methods & Techniques
In face anti spoofing, here are two principal types of Presentation Attack Detection (PAD): Hardware and Software-based.
Hardware-based PAD
To achieve better anti-spoofing and face liveness detection results, standard iris sensors are supported with specialized sensors that can measure biological characteristics of an eye. These characteristics include eye tissue density, blood vessel structure, collagen fibers, etc.
- 3D imaging. Eye geometry and curvature help prevent presentation and replay attacks. This method employs a near-Infrared light source, plus a simple 2D sensor. Together they analyze shadows on a person’s iris, which are created by uneven illumination. Multiple images are also acquired to measure depth of an eye.
- Multispectral imaging. An eye consists of three anatomical layers, each of which has its own spectrographic parameters. If a spectrographic print of an eye is obtained, it will be possible to assess whether it’s real or synthetic — substitute materials have radically different spectrographic data.
- Electrooculography. Electrooculogram is a signal stemming from cornea-retinal standing potential. This method is highly accurate in liveness detection but is invasive as electrodes should be placed in the eye region.
These methods are alternatively known as sensor-based approaches.
Software-based PAD
Software-based methods imply feature extraction and analysis. They are separated into static and dynamic approaches. (As opposed to a static, dynamic approach that analyzes multiple iris images put in a sequence.) The proposed techniques focus on:
- Applying machine learning.
- Detecting imperfections intrinsic to a printed photo.
- Exploring quality differences between real and photographed irises.
- Analyzing gray level values, color, and edges acquired from pixel-level features.
These methods include such techniques as wavelet analysis, Fourier image decomposition, local descriptors, Laplacian transform, and others.

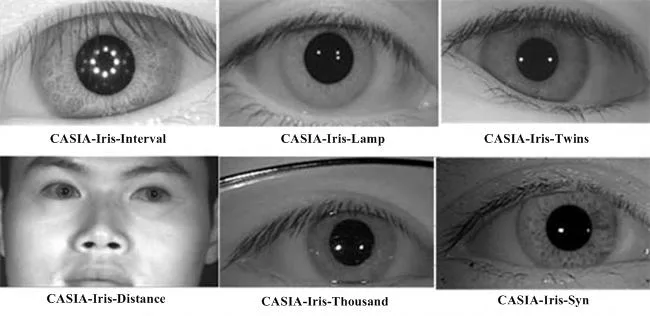
Iris Datasets
There’s an extensive variety of iris datasets: 158 in total, some of which are publicly available. Perhaps the first-known dataset was the UAE database used by prof. Dougman in the early 2000s. The first free available dataset CASIA v. 1 was released in 2003 by the Center for Biometrics and Security Research.
Currently, a number of datasets are available for use:
- CASIA-IrisV4
- ND-CrossSensor-Iris 2012
- UFPR-Periocular Dataset - V1
- ND-IrisTemplate-Aging 2008–2010
- Warsaw-BioBase-Smartphone-Iris v1.0
- WVU Synthetic Eye Dataset (may be locked for researchers outside the USA)
It should be noted that certain public databases require completion of a usage agreement or are available to academic researchers only.

Iris Recognition Performance Metrics
Performance of an iris detection system is assessed with 4 metrics:
- Attack Presentation Classification Error Rate (APCER) — percentage of PAs erroneously classified as bona fide presentations.
- Bona Fide Presentation Classification Error Rate (BPCER) — percentage of bona fide presentations erroneously classified as PAs.
- Imposter Attack Presentation Match Rate (IAPMR) — percentage of the spoofing attacks that were successfully matched.
- Concealer Attack Presentation Non-Match Rate (CAPNMR) — percentage of successful concealer attacks.
Note: CAPNMR metric is similar to the False Non-Match Rate used in identity verification.
FAQ
What are the main iris liveness detection competitions?
There are three primary challenges at iris liveness detection.
The most important iris liveness detection competition is LivDet-Iris — a part of the contest series dedicated to biometrics. Debuting in 2013, the event was in compliance with the ISO/IEC 30107-3 standard — it resulted in usage of such metrics as APCER/BPCER rates, and others.
The challenge included several attack types: printed photos, cadaver eyes, prosthetics, textured lenses, etc. The best solution, based on a Convolution Neural Network (CNN), reached a 29.78% ACER rate.
Other contests include MobiLive with iris liveness solutions for mobile and Cross-Spectral Iris/Periocular Competition (Cross-Eyed).
References
- Iris recognition by Wikipedia
- Alphonse Bertillon
- Prof. John Daugman patented the first iris recognition algorithm
- High confidence visual recognition of persons by a test of statistical independence
- LG IrisAccess 2200
- ‘Table of human iris nuances’ was proposed by the French police officer Bertillon in 1892
- UIDAI/Aadhaar program
- Introduction to Presentation Attack Detection in Iris Biometrics and Recent Advances
- Samsung builds the world’s highest-resolution phone camera sensor: 200 MP
- The 4 Main Types of Iris Patterns You Should Know (With Images)
- Artificial Eye
- A high-quality surgical eye prosthesis
- Would an iris scan work if you were unconscious or your eyeball was detached?
- The electrooculogram
- A survey of iris datasets
- Center for Biometrics and Security Research
- CASIA-IrisV4
- ND-CrossSensor-Iris 2012
- UFPR-Periocular Dataset - V1
- Warsaw-BioBase-Smartphone-Iris v1.0
- WVU Synthetic Eye Dataset

 Antispoofing
Antispoofing


