Definition & Problem Overview
In liveness taxonomy, fingerprint liveness is a security technique, which serves to deny system access to Presentation Attacks (PAs) performed with a fingerprint replica of a legitimate user. Fingerprint recognition technology was initially developed in 1975 at NIST, where scanners were used to successfully extract fingerprint points. However, the first studies on fingerprint liveness spoofing emerged only in the early 2000s when a Japanese researcher Tsutomu Matsumoto used clear gelatin to simulate a presentation attack against a fingerprint scanner. The attack was successful at fooling 11 devices.

Fingerprint verification became a mainstream phenomenon with the advent of the smart gadgets. Even though some phones have been equipped with fingerprint sensors since 2004, the first smartphone to feature such a sensor was Motorola Atrix released in 2011. The iPhone 5 was introduced two years later featuring the first Touch ID. This prompted another research, which confirmed that fooling a phone fingerprint sensor is considerably easier as most phone scanners capture fingerprints partially. Therefore, potential for spoofing or false acceptance access grew dramatically. Another cause for concern comes from the fact that counterfeit fingerprints can be crafted from various materials to imitate biometric liveness. These materials are both widely available and specialized such as dental impression substances, gelatin, silicon, play-doh and even gummy bear candy. Finally, a today's smartphone is a 'master key' to a whole network of smart domestic gadgets, which calls for a reliable anti-spoofing for IoT.
Types of Fingerprint Presentation Attacks
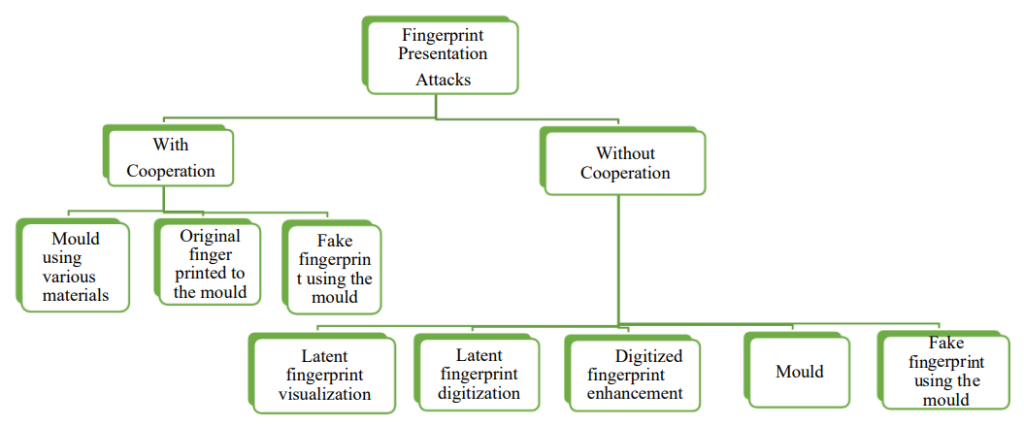
Fingerprint presentation attacks can be initiated in a number of ways based on the use of presentation attack instrument (real, fake, fabricated fingerprints) to method of attack (coercion, online theft, hacking etc.).

As reported, there are three primary types of fingerprint scanning:
- Optical. This is the simplest scanning method. It merely captures the image of a fingerprint, and is therefore, quite vulnerable to the PAs.
- Capacitance. This method uses capacitors integrated into smartphones and offers more accurate and reliable antispoofing. However, the capacitors used can malfunction due to electrostatic discharge from user fingertips.
- Ultrasound. Scanning is possible with ultrasound, which captures the friction ridge of a fingerprint. This type of scanning is theoretically the least vulnerable to PAs.
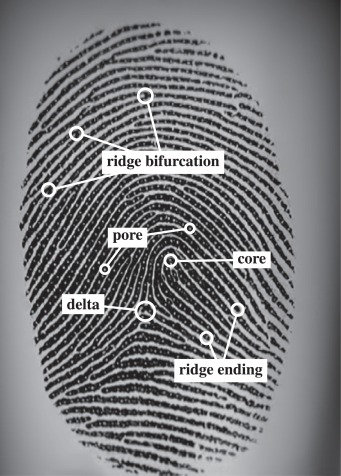
After scanning, the most important step in fingerprint detection is matching it to an existing database using various algorithms. The most popular print-matching algorithm is minutia matching. It analyzes information about the accessor’s finger ridges: where they end, where they split into two (bifurcation), etc.
Presentation Attacks aim to bypass these methods with the help of various techniques and tools. Experts highlight the following attack types:
- Severed finger scenario. An exotic case, in which a deceased person’s finger can be cut off and used for authentication. However, many researchers discard this method as ineffective. Practice shows that a finger devoid of vitality signs fails to be identified, as it produces no electricity conductance.
- Spoofing attack. A more common type, which involves a vast repertoire of Presentation Attack Instruments (PAIs). Among them are fake fingerprints fabricated using silicone, gelatin, soft rubber EcoFlex, latex, play-doh, matte paper, wood glue, latex body paint, as well as elastomeric impression materials used in dentistry.
Theft methods also vary. A target can leave their fingerprint through cooperation, while being intoxicated, threatened or unaware. Other methods allow stealing them remotely from leaked databases: 1.1 million fingerprints were stolen in 2021 as part of a hacking attack series. Another method is fingerprint jacking where a user downloads a malware app masqueraded as a benign application and is tricked to leave their fingerprint on it through its content.

A peculiar example of a remote fingerprint theft occurred in 2015, when a Chaos Communication Congress member demonstrated fingerprints of Germany’s defense minister Ursula von der Leyen, which were replicated from a few high-definition photos.

Attack Detection Methods
Two main Presentation Attack Detection (PAD) approaches are proposed. They include hardware and software approaches.

Hardware Methods
Hardware methods rely on extra gear, which allows monitoring of heart-rate oximetry, perspiration, temperature, odor, and electrical parameters of the fingertips, ensuring reliable liveness detection. While capable of detecting vitality signs, the approach also comes with higher costs, mobility limitations, as well as challenges such as environmental dependence including external weather conditions that can affect skin temperature, etc.

Software Methods
Software based approach focuses on feature extraction and analysis that is achieved with dynamic, static or combined programming, machine learning, neural networks, etc. Commonly applied techniques include wavelet decomposition, fractional Fourier transform deviation measuring, fingertip morphology/smoothness analysis, and others.

Using Neural Networks in Fingerprint Liveness
Presentation Attack Detection in fingerprint liveness relies on Convolutional Neural Networks (CNNs) that can serve as feature extractors or classificators. Some proposed methods of using CNNs are:
CNN-VGG

CNN-VGG employs an optimized CNN with an SVM used for classification. Local Binary Patterns (LBP) are used as a baseline method, while also functioning as an illumination invariant descriptor. It achieves high accuracy — 2.9% ACE — thanks to pretraining on natural images and subsequent tuning with fingerprint images. CNN-VGG proves to be superior when compared to CNN-Alexnet and CNN-Random models as the former was trained on three Liveness Detection Competition datasets (LivDet).
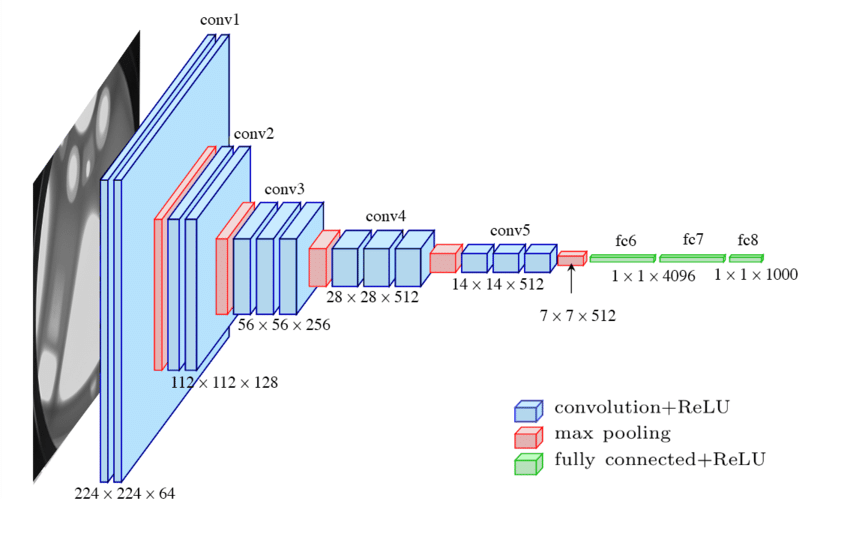
Deep-Belief Network (DBN)
This approach involves a multilayered Boltzmann machine, which is trained on a dataset with bona fide, synthesized and augmented data. The LivDet 2013 test showed a 97.10% accuracy.
CNN triplet
This solution relies on the triplet objective function variant, which analyzes fingerprint pictures and differentiates fake and real fingerprints by detecting the distance between feature points.
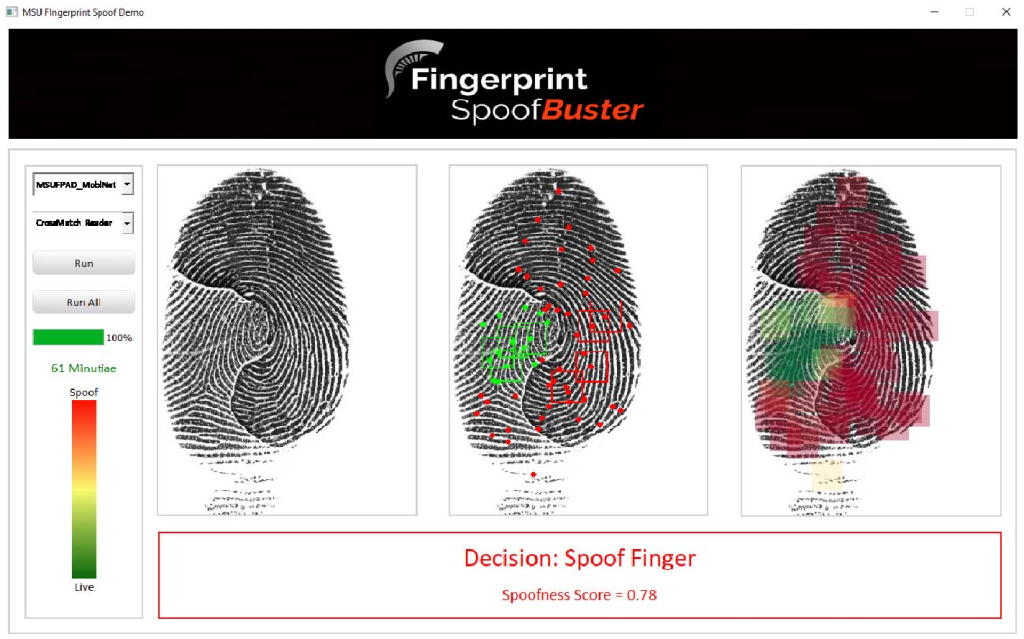
CNN & minutiae analysis
For training the network, aligned and centered local patches with 96 x 96 pixels were applied. Each training sample would receive either 1 or 0 score, where 1 means that the fingerprint is fake. (Softmax layer was used for this evaluation). Moreover, it features Fingerprint Spoof Buster — a GUI, which enables a human observer to do their own additional examining.
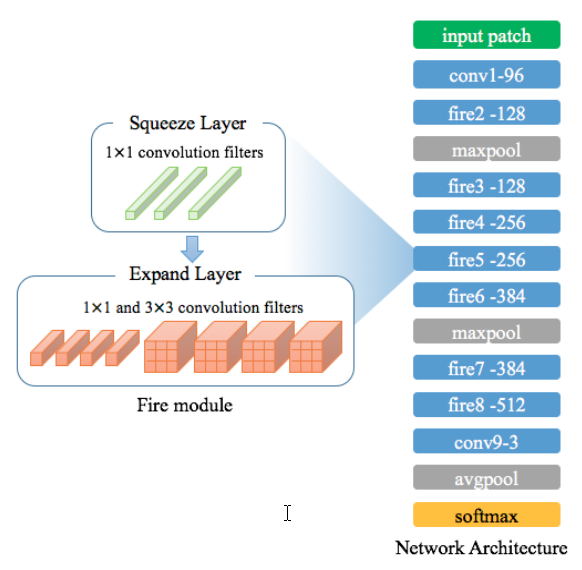
SqueezeNet
Fire Module of SqueezeNet is a cost-efficient solution, which requires only 2 MB of memory. The solution is based on the optimal threshold that allows to reduce misdetections. Tested with three LivDet datasets it demonstrated a 1.35% ACE rate with a 48 x 48 pixel patch size.
Other CNN-based solutions are offered as well: lightweight residual Slim-ResCNN, squared error layer CNN trained with fingerprints directly, CaffeNet + GoogleNet + Siamese trifecta, and so on.
Fingerprint Anti-spoofing Databases
There are a number of fingerprint datasets, some of which are:
LivDet database
A series of LivDet datasets was released from 2009 to 2021. For the LivDet 2021, sample material was collected from Green Bit DactyScan84C and DermalogLF10 scanners. The dataset contains 11,770 images obtained from various people.
NIST database
NIST offers three Special Databases 300-302, two of which are released as part of the N2N challenge. For example, SD 302 contains about 95 GB of various data: latent distal phalanx images, palm and fingerprint images segmented from upper palms, etc.

FVC
FVC has four datasets DB1-DB4, samples of which were either obtained with optical and thermal sweeping sensors or completely synthesized.
Fingerprint Liveness Detection Competition
A number of challenges dedicated to fingerprint liveness detection have been organized in recent years.
N2N Challenge
Nail to Nail (N2N) (2018-19) was an unassisted rolled fingerprint capture device challenge program hosted by NIST and supported by the US government together with IARPA. The goal of the contest was to develop a rolled capture device solution that would not involve an operator, while providing high-quality fingerprint images.
LivDet
LivDet is an ongoing contest hosted by the Department of Electrical and Electronic Engineering and University of Cagliari. Its goal is to find the most effective solution for detecting spoofing attacks against fingerprint verification systems. It consists of three stages, the last one being the Hidden challenge featuring "unknown sensors".
FAQ
Is it possible to protect the system from fingerprint spoofing attacks?
Biometric systems can be prevented from fingerprint spoofing via fingerprint liveness detection. Spoofing attacks are a common threat to systems based on fingerprint scanning. In most cases, fraudsters steal a fingerprint database and replicate the target’s fingerprints using gelatin, silicon, dental impression material, and other similar substances.
Fingerprint liveness detection can be used to prevent spoofing attacks. As highlighted by Antispoofing.org Wiki, It employs techniques such as minutia analysis with a Convolutional Neural Network, Deep-Belief Network, as well as physical scanners that can detect heart-rate oximetry, electrodermal activity, odor, temperature, and other properties of a real finger.
Fingerprint liveness — Definition
Fingerprint liveness is a set of characteristics inherent to the fingerprint of a living human.
Fingerprint liveness is defined by the physiological features intrinsic to a human finger. These include electrodermal parameters, temperature, pulsation caused by heart activity, odor, perspiration, as well as friction ridges that form a fingerprint itself.
Fingerprint liveness detection analyzes all of these parameters to distinguish a real finger from a counterfeit. This helps to prevent spoofing attacks that are performed with the help of fake fingerprints made from various elastic materials.
Fingerprint liveness is an essential part of liveness detection, especially in multimodal systems.
What are the main types of fingerprint presentation attacks?
There are two primary types of fingerprint Presentation Attacks. The technique used in a fingerprint presentation attack (PA) is directly related to the detector/ scanner it aims to bypass. There are three types of fingerprint scanners:
- Optical. It ‘photographs’ the fingerprint image.
- Ultrasound. It uses ultrasound waves to scan the fingerprint ridges.
- Capacitance. It employs small capacitor array circuits to collect data.
Fingerprint Presentation Attacks (PAs) aim to bypass these sensors with spoofing. For that purpose, fake fingerprints are produced from latex, gelatin, Play-Doh, elastomeric dental materials, etc.
A PA type known as Severed Finger scenario, in which a dead person’s finger can be used for verification, is mostly rejected as ineffective due to the lack of electric conductance in a lifeless finger.
How to detect fingerprint presentation attacks?
A fingerprint presentation attack can be detected with hardware and software methods.
Fingerprint presentation attacks can be detected using two methods:
- Hardware. This approach employs extra equipment that can detect and assess biological parameters native to a live human finger: electric signals, perspiration, natural skin texture, odor, heart-rate oximetry, and other features.
- Software. Machine learning and neural networks are used for extracting and analyzing fingerprint features, including minutiae analysis. Among the tools are SqueezeNet, Deep-Belief Network (DBN), etc.
How to use neural networks for fingerprint liveness detection?
A number of neural networks have been designed for detecting fingerprint liveness.
Fingerprint liveness detection mostly benefits from the usage of Convolutional Neural Networks (CNNs). Their primary functions are feature extraction and classification. Therefore, a number of CNN architectures are offered to prevent fingerprint spoofing attacks:
- CNN-VGG. This solution offers a high detection accuracy thanks to pre-training on a variety of regular photos.
- Deep-Belief Network (DBN). Based on a multilayered Boltzmann machine, it demonstrates a 97.10% accuracy.
- SqueezeNet. This approach includes an optimal threshold, which helps minimize misdirection, while being cost-efficient.
More similar solutions are expected to emerge with time.
References
- One of the earliest fingerprint identification examples in history (by W.J. Hershel)
- Biometric Technology: A Brief History
- What is gummy bear hack?
- Fingerprint scanner on Phones: History and Evolution, but do we really need that?
- Motorola Atrix 4G
- Apple Announces iPhone 5s—The Most Forward-Thinking Smartphone in the World
- MasterPrint: Exploring the Vulnerability of Partial Fingerprint-Based Authentication Systems
- Gummy Bears can be used by hackers to make a counterfeit fingerprint to fool your scanner
- A comprehensive survey of fingerprint presentation attack detection
- Fundamentals of fingerprint scanning
- Fingerprint Minutiae Matching Based on the Local and Global Structures
- Fingerprint indexing based on minutiae pairs and convex core point
- Robust anti-spoofing techniques for fingerprint liveness detection: A Survey
- Why Dead Fingers (Usually) Can't Unlock a Phone
- Dental Impression Materials
- Massive Fingerprint Hack Illustrates Why Anonymous Biometrics Are Critical To Security
- 'Fingerprint-Jacking' Attack Technique Manipulates Android UI
- Hacker fakes German minister's fingerprints using photos of her hands
- Fingerprint Liveness Detection using Convolutional Neural Networks
- VGG architecture
- Fingerprint Spoof Buster: Use of Minutiae-Centered Patches
- Patch-based Fake Fingerprint Detection Using a Fully Convolutional Neural Network with a Small Number of Parameters and an Optimal Threshold
- LivDet Databases
- Biometric Special Databases and Software
- A Survey on Antispoofing Schemes for Fingerprint Recognition Systems
- FVC has four datasets DB1-DB4
- Nail to Nail (N2N) Fingerprint Capture Challenge
- IARPA
- LivDet
- Dipartimento di Ingegneria elettrica ed elettronica

 Antispoofing
Antispoofing



