Liveness Definition
In liveness taxonomy, Liveness Detection (or biometric anti-spoofing, or biometric liveness) is a set of preventive measures, which ensure that original or mimicked biometric authorization data cannot be used by impostors for purposes of theft or fraud.
Anti-spoofing and liveness detection are being actively adopted throughout numerous industries including banking, online payments, medicine, mobile phones, commercial security systems, or state security as it’s prescribed by the liveness standards. Liveness definition, in turn, includes a group of parameters intrinsic to a living person. The need for liveness detection and anti-spoofing was created due to the emergence of numerous techniques and options of identity replacement on the Black market. These methods range from primitive usage of stolen portrait photos and deepfake videos to highly complex techniques involving hyper realistic human face masks made of plasticine, silicone, latex, and even materials like conductive liquid polyamide solution that is capable of imitating the touch of human skin.
Biometric anti-spoofing plays a major role in today’s security systems, as it is able to differentiate real humans and their body parts (biometric liveness) from artificial replicas. Therefore, it has become a necessary tool to raise the effectiveness and reliability of biometric security systems.
Types of Biometric Anti-spoofing
Biometric anti-spoofing covers a broad spectrum of practical applications including handwriting recognition, fingerprint verification, iris and retinal scanning etc. On the other hand, liveness detection is mostly limited to facial recognition, voice identification, and, a certain level of behavioral characteristics, which can also be attributed to the liveness definition.
What is a Presentation Attack?
Presentation attacks are the main source of threat challenging biometric systems. A presentation attack is defined as:
A Presentation attack takes place when a spoofing tool is presented to a biometrical system.
Presentation attack (PA) is a type of attack, during which a spoofing artifact that emulates biometric liveness is presented to the sensors of a targeted system.
These artifacts include a vast repertoire of crime tools: fake fingerprints made from gelatin, printed photos, elaborate silicone masks, [[Facial Deepfakes|facial deepfakes]], artificially synthesized voice recordings, etc.
Antispoofing solutions and spoofing detection are designed to combat these attacks. They analyze whether the presented biometric data — eye retina, fingerprints, human voice or face — are genuine or not.
Sometimes presentation attacks are accompanied by indirect attacks.
There are various methods a Presentation attack can be initiated or presented to the system.
Facial Anti-spoofing
According to Data Science, facial recognition is the second most popular identification technique, next to fingerprint scanning.
According to liveness standards, there are two main facial recognition attack types: indirect and presentation. While the indirect attack requires a perpetrator to access the interior of the system, presentation attack aims at the sensor level, faking the biometric liveness.
Presentation attacks are seen as the primary source of threat when it comes to spoofing a biometric system. Attackers can carry out a PAD using the following methods:
- Printed Photo. An impostor simply shows a targeted person’s photo to the recognition system. The picture quality may vary.
- Display Attack. A clip containing the image of a user (or a single image) is shown to the camera of the system.
- 2D Mask. The method involves a mask cut out of paper with a face texture
- 3D Mask. A more elaborate method involves a silicon mask, 3D head sculpture, or wax figure, which mimics the user’s face.
- Other. State-of-the-art makeup and plastic surgeries are used as possible attack tools.
To combat these types of spoofing, various methods are suggested. In general, these methods are classified as Active and Passive Facial Anti-spoofing.
Passive methods include frequency and texture-based analysis, Fourier spectral analysis, variable focusing which relies on Depth of Field and Sum Modified Laplacian values, monitoring of eye movement and shape variations through sequential photos, and optical flow analysis (combination of eye movement patterns) etc.
In addition to these methods, solutions based on artificial intelligence and deep learning are also used. They include residual neural network, high frequency, and local binary pattern descriptors, and other similar techniques that explore characteristics mentioned by the liveness definition.
Active Facial Anti-spoofing methods take a more active approach, as a person is asked to do a certain request — smile, blink, raise eyebrows — to double-check the person’s identity.
When combined, these methods form a Presentation Attack Detection (PAD) system which can be integrated into the existing biometric security systems.

Voice Anti-spoofing
Voice spoofing, often featured in voice phishing, targets an Automatic Speaker Verification system (ASV). This system is widely adopted by banks and other financial services, as well as used in the voice-unlocking features integrated into mobile phones.
Similar to facial anti-spoofing, voice liveness recognition deals with direct attacks only. Indirect attacks explore technical vulnerabilities of the AVS, such as poorly protected transmission channels.
There are two attack types that make voice spoofing possible. The first type involves a simple voice recording obtained through methods like hacking and social engineering etc.
The second type is based on impersonating the target’s voice. This type of threat is causing concern due to the emergence of a large number of voice-imitating neural networks similar to Voice AI — which is capable of generating believable voice acting.
Apart from cloning, such neural networks can also disguise an attacker’s voice to mimic that of a legitimate user. To counter this issue, researchers have propose anti-spoofing techniques with the central concept of obtaining additional acoustic information to help the system detect the biometric liveness and decide whether the user is a human speaker or not.
Security and liveness standards state that AVS systems should be protected accordingly. One solution is based on analyzing the time-difference-of-arrival that can be observed in phonemes uttered by a living human and define their "speech uniqueness", which is seen as one of the parameters described by the liveness definition.
The same study by NEC Corporation also mentions the "pop noise" approach. It implies identifying speech as live or fake, depending on whether the so-called pop noise is present or not.
Pop noise originates when the microphone of a mobile phone picks up random breathing noises or noises produced by the plosive consonants: [p], [b], [k], [g], and others.
Another known technique to prevent voice biometric spoofing is called Void — Voice liveness detection. This open-source solution is based on a simple comparison of vocal spectrograms and does not require deep learning.
Using vocal spectrograms, Void can identify whether the voice is live or not by comparing their sound intensity. It is observed that a recorded voice lacks certain acoustic frequencies and cannot deliver the vocal "fullness", which a real voice can, which contributes to vocal spoofing detection.

Other types of Anti-spoofing
Fingerprint recognition, avidly mentioned in the liveness definition, is still the most popular target among malicious actors. Fingerprints can be obtained through various ways like hacking: in 2015, 5.6 million fingerprints were stolen from Washington’s Office of Personnel Management.
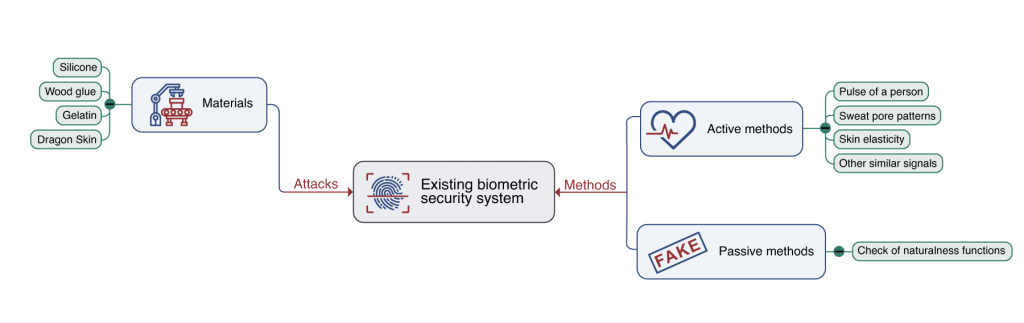
To perform this type of biometric spoofing, attackers can replicate stolen fingerprints with various tools and materials including silicone, wood glue, gelatin, and even Dragon Skin typically used for movie productions.
In fingerprint recognition, liveness detection can be achieved using active and passive methods. The active approach verifies authenticity based on the pulse of a person, sweat pore patterns, skin elasticity (almost impossible to imitate) and other similar signals.
On the other hand, passive methods focus on unnatural details of the fingerprint such as lack of certain features that only a real human finger exhibits.
Another form of attack is Iris spoofing. The two most common threats are presentation attacks that involve a high-definition photo of an eye or contact lenses selected to imitate the target’s eyes.
Another form of spoofing that is gaining the attention of security experts are attacks carried out using artificial eye replicas.
Possible biometric spoofing countermeasures proposed by researchers include detection of certain behavioral characteristics. For instance, the system can detect authenticity based on hippus — tiny oscillatory movements that happen as a natural reaction to light that are possible only in a real human iris.
Spectrographic data of different eye components — such as melanin pigmentation — can also be used to detect a spoofing attempt.

Standards/Certification
Biometric anti-spoofing technologies have to be designed in compliance with some security and liveness standards in order to establish their reliability. Basically, these standards are largely predefined by the liveness definition.
ISO/IEC 30107 Standard
There are two major liveness standards. ISO/IEC 30107 standard was accepted by the International Organization for Standardization together with the International Electrotechnical Commission in 2016.
The ISO/IEC certification pre-defines how attacks and system vulnerabilities should be classified and assessed. It also dictates algorithms and countermeasures for tackling these attacks.
FIDO
FIDO (from Latin fido — trust) stands for Fast Identity Online. This is an array of security protocols, which allow a quick and safe identity verification without password usage.
FIDO encompasses solutions such as near-field communication, security tokens, and biometric identification, which is secured with additional standards like Universal Second Factor (U2F) etc.
FAQ
What is liveness?
Liveness is a set of qualities that differentiates a non-living object from a real human.
Liveness is a set of characteristics that is ascribed to a living person. It includes various biometric data. Principal liveness parameters include a person’s voice, fingerprints, facial features, and heart rate. At the same time, behavioral characteristics, physiological properties (like skin elasticity), and physical data also play a major role in identifying a living human.
Liveness is used as the essential criterion in liveness detection and antispoofing. The term "liveness" is believed to have been proposed for the first time by Dorothy E. Denning in her article It's "liveness," not secrecy, that counts.
What is passive liveness detection?
Passive liveness detection is a type of biometric verification that does not need a person to perform any additional actions to get verified.
Passive liveness detection is a method of biometric identification. It does not require a person to perform any actions such as nod, smile, blink, talk, or move to confirm their identity. Passive identification is considered more convenient and favorable by most users when compared to active identification. It provides a better user experience and requires less verification time. Another advantage of passive liveness detection is its silent and hidden mode of operation. It does not alert users that biometric identification is taking place, so malicious actors stay unaware and unprepared.
What is antispoofing?
Antispoofing is a set of countermeasures designed to work against biometric attacks.
Antispoofing is a set of techniques to prevent liveness attacks. It is aimed at differentiating fabricated or synthesized body parts, anatomical traits and media from real user identities. Spoofing attacks cover a wide range of techniques targeting facial features, voice, fingerprints, retina, and other biometric data.
Similarly, Antispoofing comprises a variety of sophisticated techniques that can detect spoofing attacks with a high accuracy rate. Liveness attacks and deepfakes can result in serious financial, reputational and social damage. Therefore, antispoofing is a vital security component of modern businesses, media, public services, law enforcement, and national agencies.
What are the main methods of machine spoof detection?
Computer liveness detection depends on a variety of high accuracy techniques
Computer detection is considered superior in antispoofing compared to human capacity. Computer detection uses various methods with a few highlighted below:
- Temporal sequential analysis. It is used to detect face swapping.
- Data modalities detection. Observes audio spectrograms, audio-video inconsistencies, etc.
- Lighting analysis. Uses colored flashing, which helps analyze how light reflects off a target’s face.
- Heart rate estimation. Analyzes heart activity of a person through subtle color shifts in their skin.
- MAD. Prevents morphing attacks by spotting "clues" left by the morphing process.
Apart from these, many new techniques routinely appear in response to the growing threat of face manipulation.
Which techniques can be used for anti-spoofing?
Antispoofing covers a wide range of preventive techniques that can stop or mitigate spoofing attacks.
Antispoofing suggests multiple ways to prevent presentation attacks (PA). The preventive technique used depends on the type of a biometric system in question. For instance, antispoofing of voice recognition systems can be done with the help of POP-method. Internet of Things (IoT) systems can be protected with encryption, CSI-data analysis, and anti-jamming.
On the other hand, face recognition systems rely on sophisticated antispoofing solutions including 3D cameras, infrared sensors, and deep convolutional neural networks etc. As a result of modern technological advancements, the number of spoofing attacks has grown. Therefore, techniques employed by malicious actors require more effective antispoofing solutions.
How does antispoofing work?
Antispoofing is a group of techniques that prevent illegal usage of authorization data.
It uses numerous methods and tools called liveness detection techniques to prevent spoofing attacks. Antispoofing techniques for facial recognition systems are regulated by standards and certifications like NIST ISO/IEC 30107 or FIDO.
Liveness antispoofing analyzes biometric data — vocal tonality/timbre, fingerprints, eye retina, facial features — to prevent impersonators from illegal authorization. The goal of antispoofing is to detect whether the person identified by a biometric system is who they claim to be and if they are real. Antispoofing measures are also aimed to detect whether a person is being forced to get authorized by a biometric recognition system.
What is spoofing?
Spoofing is an act of impersonation, often used in cyberattacks.
Spoofing is an act of posing as an authentic trusted person, organization, or system, typically for illegal purposes. This technique is widely adopted by malicious actors for the sake of gaining access to sensitive data, money, and other valuable resources.
Spoofing targets a broad range of applications: emails, IP addresses, Domain Name System, GPS, and so forth. Liveness spoofing has become widespread with the advent of mobile devices and autonomous technologies. The key targets are fingerprint, facial, and voice recognition systems. Liveness spoofing is seen as a major threat to personal, corporate, and national security.
What is biometric spoofing?
Biometric spoofing refers to the process of presenting fake replicas of human body parts to authentication systems for the sake of gaining illegal access.
Biometric spoofing is a malicious practice employed by impostors against online and offline authentication systems. It includes various techniques and instruments to fool a biometric authentication system into believing that the presented person/object is a legitimate user.
Biometric spoofing can be carried out by using fake fingerprints, pre-recorded/synthesized voice samples, realistic silicone masks, video deepfakes, printed photos, etc. It is done to gain access to information, money, and other valuables. With the advent of mobile technology, spoofing attacks have become a frequent issue. Experts believe that biometric spoofing also presents a potential threat to national security.
What is biometrics?
Biometrics is the measurement and analysis of people's unique anatomic and behavioral characteristics.
Biometrics is a group of unique physiological and behavioral traits. They help differentiate one person from another — as not a single human has biometrics identical to that of another person. Liveness detection is based on biometric analysis and includes the detection of unique features such as face, voice, fingerprint, iris, handwriting, etc.
Human behavior also forms an important part of biometrics. Habits are a major building block of personality and can be used for analysis and unmasking of possible fraud attempts. For example, unusual shopping activity or irregular cash withdrawals that are not aligned with a user's normal behavioral traits may indicate a security breech.
How does liveness work with biometrics?
Liveness detection requires biometric data to verify or reject a person.
Liveness detection is the ability of a system to accurately differentiate a fake body from a real one. By analyzing physical, chemical and anatomical properties, a liveness detection system concludes whether the presented person is real or not. These systems are employed as a counter measure to spoofing techniques that have advanced considerably over the years. Modern attackers/ malicious actors employ complex and sophisticated means for spoofing attacks such as:
- Conductive liquid polyamide solution for imitating fingerprints.
- Convolutional Neural Networks (CNNs) for synthesizing highly realistic voices.
- Elaborate 3D silicone masks for facial spoofing attacks.
Liveness detection aims to filter out potential attacks by countering advanced spoofing techniques. Biometrics are the key data source that allow liveness detection to detect irregularities and fake persons.
What are the most promising types of biometric identification and biometric liveness detection?
There are several modalities seen as quite promising by the researchers.
Iris liveness detection, retina and, to an extent, electrocardiogram recognition are considered auspicious by the researchers. Iris and retina have highly unique properties — such as pigmented rings in iris — that make them even more accurate than fingerprint recognition. With the usage of proper equipment, like telescopic cameras, both these modalities retain a lot of potential.
Electrocardiogram recognition (ECG) is also promising as it’s deeply individual in every person’s case. It’s already utilized in wearable authentication devices, but some research shows that ECG signals can be intercepted and spoofed.
What are the most largely deployed types of biometrics?
Face and fingerprint recognition are the leading biometric modalities.
A number of surveys and researchers report that fingerprint recognition still remains the most popular biometric modality — in 2018 alone 96.5% of all smartphones were equipped with capacitive fingerprint technology. Face recognition is the second most popular modality that received the title of the most exciting modality in 2019.
Voice and iris detection modalities also look quite promising. Among all else, the voice biometrics market is forecast to reach a 30.1 billion value by 2027. Multimodal authentication and anti-spoofing systems seem to be gaining more exposure and usage as trends show. (See more relevant biometrics stats here.)
Is it possible to identify a person by their eyes?
Iris and retina identification allow identifying people.
Two modalities allow identifying a person by their eyes: retina and iris recognition. Iris modality focuses on such typical features as crypts, contraction furrows, pigmented rings, conjunctival melanosis, and other elements that form unique patterns and give irises their color.
Retina recognition analyzes blood vessel patterns or vasculature that consists of arteries, vessels and arterioles. Retinal anti-spoofing is reported to be extremely accurate. At the same time it’s more challenging from the technical point of view as it requires special hardware — fundus photography equipment — and cooperation from the subject.
What differentiates biometric identification, biometric verification and biometric recognition?
Recognition, verification and identification are three main components of biometric security.
Biometric recognition is responsible for recognizing a certain biometric trait — fingerprint, face, voice — effectively and accurately. Biometric identification is a parameter that helps identify a user accessing a system. It’s needed to prevent a wrong person from authorizing as someone else.
Verification is the final step. It employs liveness detection to tell fake body parts or behavioral traits from genuine. Liveness detection analyzes liveness signals — like vocal parameters in Automatic Speaker Verification — to confirm that a person accessing a system is who they claim to be and also that they are real.
References
- Nanotips website
- Facial Recognition: Types of Attacks and Anti-Spoofing Techniques
- Residual neural network, Wikipedia
- Voice phishing, Wikipedia
- Voice Liveness Detection for Medical Devices, Xiali Hei, Bin Hao, Research Gate
- Voice Imitating Text-to-Speech Neural Networks, Younggun, LeeTaesu Kim, Soo-Young Lee, Research Gate
- Witcher 3 mod uses AI to create new voice lines without Geralt’s original voice actor, GamesRadar
- POCO: a Voice Spoofing and Liveness Detection Corpus based on Pop Noise, Kosuke Akimoto, Seng Pei Liewy, Sakiko Mishima, Ryo Mizushima, Kong Aik Lee
- An Overview of Face Liveness Detection, Saptarshi Chakraborty1 and Dhrubajyoti Das
- Plosive Consonants, Wikipedia
- New technique protects consumers from voice spoofing attacks, HelpNetSecurity
- Sound Intensity, Wikipedia
- Millions of fingerprints stolen in US government hack, BBC News
- Smooth-On, Inc. website
- Anti-spoofing method for fingerprint recognition using patch based deep learning machine. Diaa M.Uliyana, Somayeh Sadeghib, Hamid A.Jalab
- A review of iris anti-spoofing. Javier Galbally, Marta Gomez-Barrero
- Hippus, Wikipedia
- ISO/IEC 30107-1:2016, ISO website
- International Electrotechnical Commission, website
- FIDO Alliance, website

 Antispoofing
Antispoofing