Everything you wanted to know about Biometric Security, Liveness Detection, Spoofing Attacks, and Antispoofing Measures, Access Control, Liveness Check, and Recognition Security Systems.

4 min read
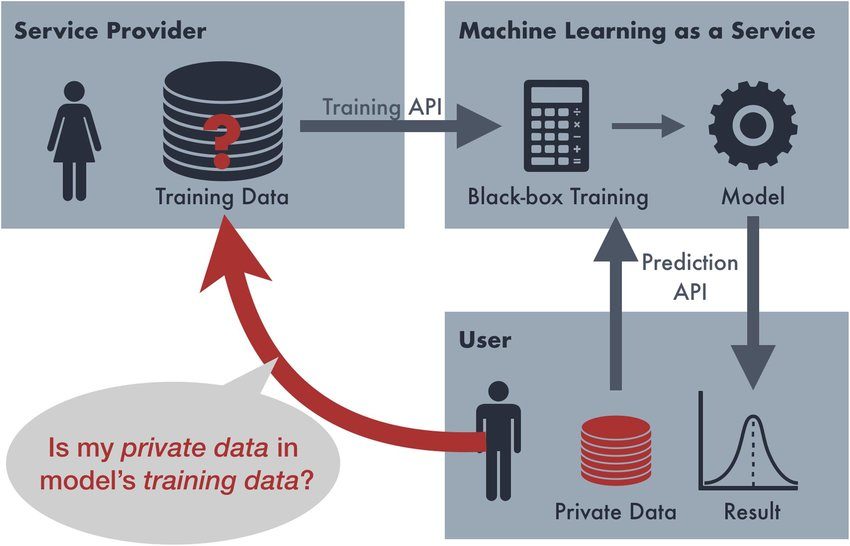
What Is Membership Inference Attack? Membership Inference Attack (MIA) is a technique that reveals if a certain data sample was used for training a deep-learning model. Generative models, apart from classifying samples, should also be able to extend their performance to handle other, previously unseen data. However, handling new and poorly explored data can somewhat
4 min read
Model Inversion Attack: Overview Model inversion is a complex attack scenario, in which a deep-learning model is trained on the output of the target model. It is done so that the input data can be predicted, which can allow tracking the target’s model initial training data corpus. Classification of Model Inversion Attacks (MIAs) Commonly, Inversiona
Antispoofing — The Key to Safety in Digital and Real Worlds
Antispoofing is an amalgam of machine learning, anatomical studies, and behavioral psychology, which solves one essential issue: keeping people’s assets and private information safe in the era when biometric data can easily be peeped and replicated.
Biometric security is a crucial aspect of our digital lives, but it's not without its vulnerabilities. Antispoofing measures are a combination of machine learning, anatomical studies, and behavioral psychology designed to keep our assets and private information safe from malicious attacks. In this encyclopedia, we'll delve into the world of liveness detection, spoofing attacks, and antispoofing measures to explore the most effective ways to combat these threats.
Spoofing attacks have become increasingly common, especially with the rise of mobile technology and the Internet of Things. These attacks involve fabricating liveness cues or synthesizing a completely falsified person to gain access to sensitive data, money, or control over devices and vehicles. The goal of antispoofing measures is to prevent these attacks and ensure the security of our biometric data.
Liveness detection is a crucial component of antispoofing measures. It allows us to avoid a wide range of fraudulent techniques and prevent identity theft. Swindlers often target various systems, including mobile phones, smart domestic appliances, and Automatic Border Control systems. By detecting liveness, we can prevent these attacks and keep our biometric data safe.
Spoofing attacks can take many forms, including voice, fingerprint, face, or heart rate replication. These attacks are often carried out remotely, making it easier for attackers to manipulate biometric security systems. The proliferation of deepfake tools has made it even easier for regular people to produce falsified media, such as face swaps, with just a few clicks. This has significant implications for our digital security and the need for effective antispoofing measures.
4 min read
Model Inversion Attack: Overview Model inversion is a complex attack scenario, in which a deep-learning model is trained on the output of the target model. It is done so that the input data can be predicted, which can allow tracking the target’s model initial training data corpus. Classification of Model Inversion Attacks (MIAs) Commonly, Inversiona
3 min read
What Is Voice Conversion? Voice conversion is a technique of adjusting someone’s voice to exactly mimic another person’s timbre, accent, articulation, and other vocal and speech parameters. In most scenarios, voice conversion can both be pre-recorded or applied in real-time thanks to various deep learning solutions. What Is Voice Conversion Attack? Voice conversion attack (VCA)
3 min read
What Are the Main Algorithms for Detecting AI-Generated Texts? There are three main approaches to detect synthesized writing: Virtually all existing detectors rely on these approaches. Is It Necessary to Distinguish AI-Generated and Human-Written Texts? It is acknowledged that an ability to accurately detect synthetic writing is crucial. Large Language Models (LLMs) can be used
The Evolution of Deepfakes
A Growing Threat to Identity Verification and Financial Security
Fraudsters using simple household items like playdough, body paint, gelatin-based candy, glue, and construction paper to mimic liveness and bypass antispoofing systems.
More sophisticated physical attacks include using highly realistic 3D masks that emulate body heat, severing a deceased person’s finger or extracting an eye, and even undergoing plastic surgery to defeat biometric verification.
Fraudsters investing months in social engineering, collecting training data to produce high-quality deepfakes, attempting reverse engineering, and exploring novel attack vectors.
3 min read
What Is a Spoofing Attack on an AI-Text Detector? AI text detector spoofing is a deliberate attempt of presenting a text created with a Large Language Model (LLM) as a human-written to a detecting solution or vice versa. Typically, it is possible by inserting small perturbations into the writing, which confuses an AI-detector, as it’s
4 min read
What Is LLM Watermark Erasing (Removing) Attack? Watermark erasing attack is an unauthorised process of removing metadata inserted in some type of media: video, image, text, and so on. Large Language Models (LLMs) and their output are also watermarked. The attack is typically orchestrated without tempering with the encryption key applied to protect the media.
Fake media detection
Fake media detection is also an essential part of antispoofing, which are designed to differentiate a real person from a perpetrator using various biometric parameters like voice, retina, iris, fingerprint, and facial recognition.
Fake media detection is crucial for antispoofing to prevent disastrous consequences such as social instability, public opinion manipulation, and defamation. Sociology experts highlight two negative phenomena induced by fake media: liar’s dividend and reality apathy.
Antispoofing techniques and liveness detection solutions analyze input data such as pop noises, face coloring, light distribution, depth and geometry, and general liveness signals to spot fake body parts, facial alterations, replay attacks, and synthesized audiovisuals.
The discussion includes the most successful methods and best tools, international antispoofing and liveness standards, attack types and their classification, terminology, and other relevant aspects. The data is validated through scientific publications and popular media dedicated to liveness security and antispoofing.
Everything you wanted to know about Biometric Security, Liveness Detection, Spoofing Attacks, and Antispoofing Measures.
Learn more about Access Control, Liveness Check, and Recognition Security Systems.
Contribute to Antispoofing Wiki
by Becoming an Author or CommenterIf you have a good knowledge of biometric security, we welcome you to take part in writing or editing articles for the Antispoofing Wiki and be among the project’s contributors. Details can be found at the link below.
If you have questions about the article topics or want to comment on them, you can use the quick registration form.